Article contents
Sequential metric dimension for random graphs
Published online by Cambridge University Press: 22 November 2021
Abstract
In the localization game on a graph, the goal is to find a fixed but unknown target node 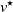 $v^\star$
with the least number of distance queries possible. In the jth step of the game, the player queries a single node
$v^\star$
with the least number of distance queries possible. In the jth step of the game, the player queries a single node 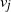 $v_j$
and receives, as an answer to their query, the distance between the nodes
$v_j$
and receives, as an answer to their query, the distance between the nodes 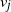 $v_j$
and
$v_j$
and 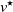 $v^\star$
. The sequential metric dimension (SMD) is the minimal number of queries that the player needs to guess the target with absolute certainty, no matter where the target is.
$v^\star$
. The sequential metric dimension (SMD) is the minimal number of queries that the player needs to guess the target with absolute certainty, no matter where the target is.
The term SMD originates from the related notion of metric dimension (MD), which can be defined the same way as the SMD except that the player’s queries are non-adaptive. In this work we extend the results of Bollobás, Mitsche, and Prałat [4] on the MD of Erdős–Rényi graphs to the SMD. We find that, in connected Erdős–Rényi graphs, the MD and the SMD are a constant factor apart. For the lower bound we present a clean analysis by combining tools developed for the MD and a novel coupling argument. For the upper bound we show that a strategy that greedily minimizes the number of candidate targets in each step uses asymptotically optimal queries in Erdős–Rényi graphs. Connections with source localization, binary search on graphs, and the birthday problem are discussed.
MSC classification
- Type
- Original Article
- Information
- Copyright
- © The Author(s), 2021. Published by Cambridge University Press on behalf of Applied Probability Trust
References
- 2
- Cited by





